Best VAPT & Cyber Security Company in Maharashtra,India

Driving Digital Trust Through Next-Gen Security Solution
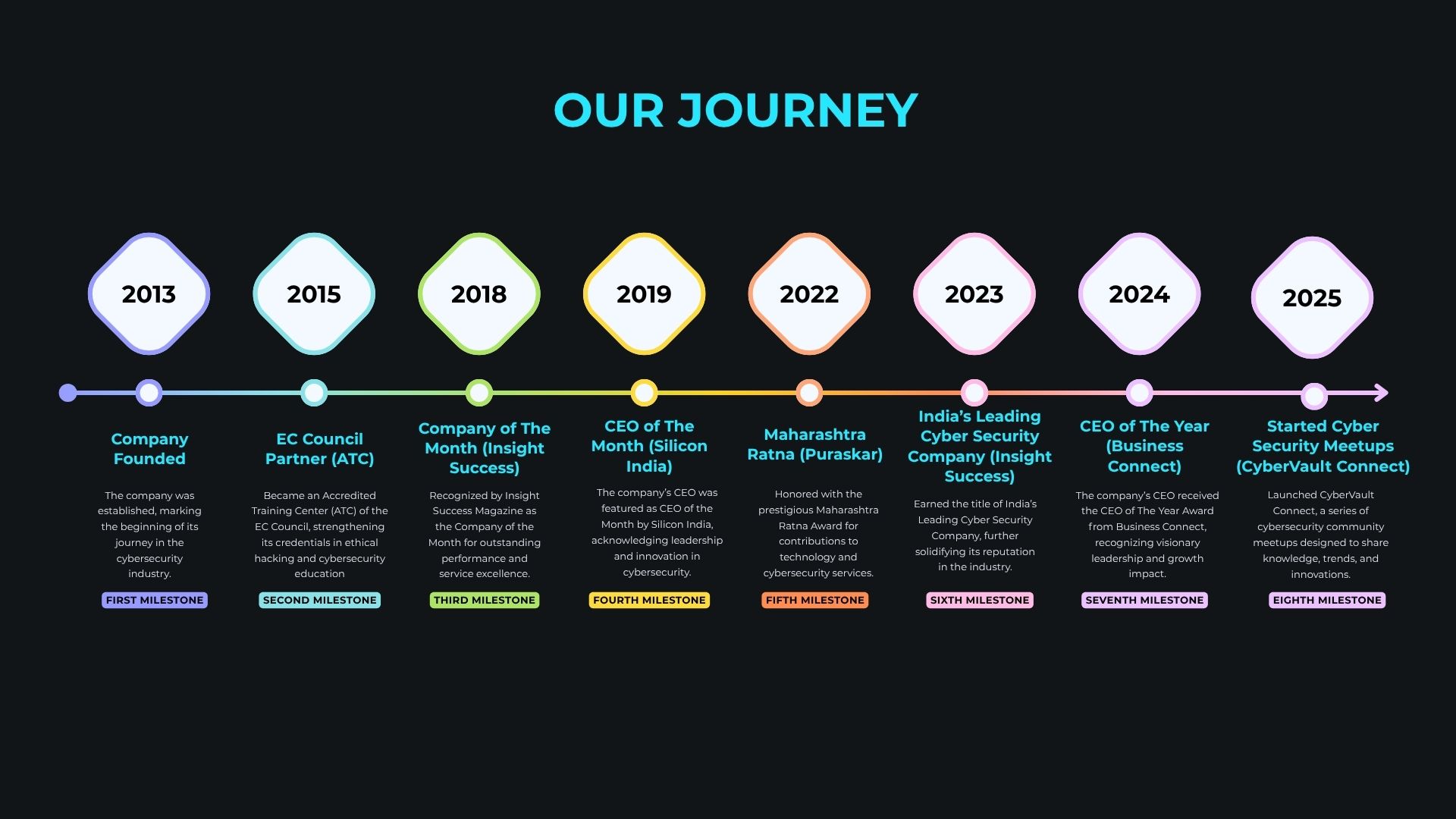
As the best VAPT and cybersecurity company in Pune, Maharashtra, safeguarding your digital assets is our top priority. We identify vulnerabilities, provide effective solutions, and ensure compliance with industry standards to fortify your digital fortress. Cybervault Securities Solutions Pvt. Ltd., based in Pune, Maharashtra, India, is a leading cybersecurity company in India, delivering trusted services and training since 2013. We specialize in IT security services, VAPT, compliance audits, managed security solutions, and EC-Council authorized training programs that empower businesses and professionals across Maharashtra and India to stay ahead of emerging cyber threats.
Vision
Mission
- Delivering trusted information security services that transform expertise into client value.
- We deliver top-quality information security services, turning our expertise into value for our clients.